Oculus2: Inside the Controller...
Controller overview
This time, I decided to dig into Oculus’s controller to see what interesting I could find there. I’m taking a closer look at the Oculus Quest 2 controller. I’ve always been curious about what makes this piece of tech tick, and now, I’m finally digging in to see what’s inside.
Without top cover
Test Pins
The first intriguing discovery can be found inside the battery compartment, concealed beneath the label: 

That is very interesting. I’m now starting to take apart the controller to examine these pins. Fortunately, identifying the pins wasn’t difficult as they are clearly labeled:  (yeah, in this photo, I already soldered wires to connect an external power source instead of a battery)
(yeah, in this photo, I already soldered wires to connect an external power source instead of a battery)
A quick examination revealed that the SWD lines are not connected to SoC pins. This leads to another finding: the SWD lines (SWDCLK and SWDIO) are physically disconnected but can be reconnected by soldering 0R resistors R2 and R1. 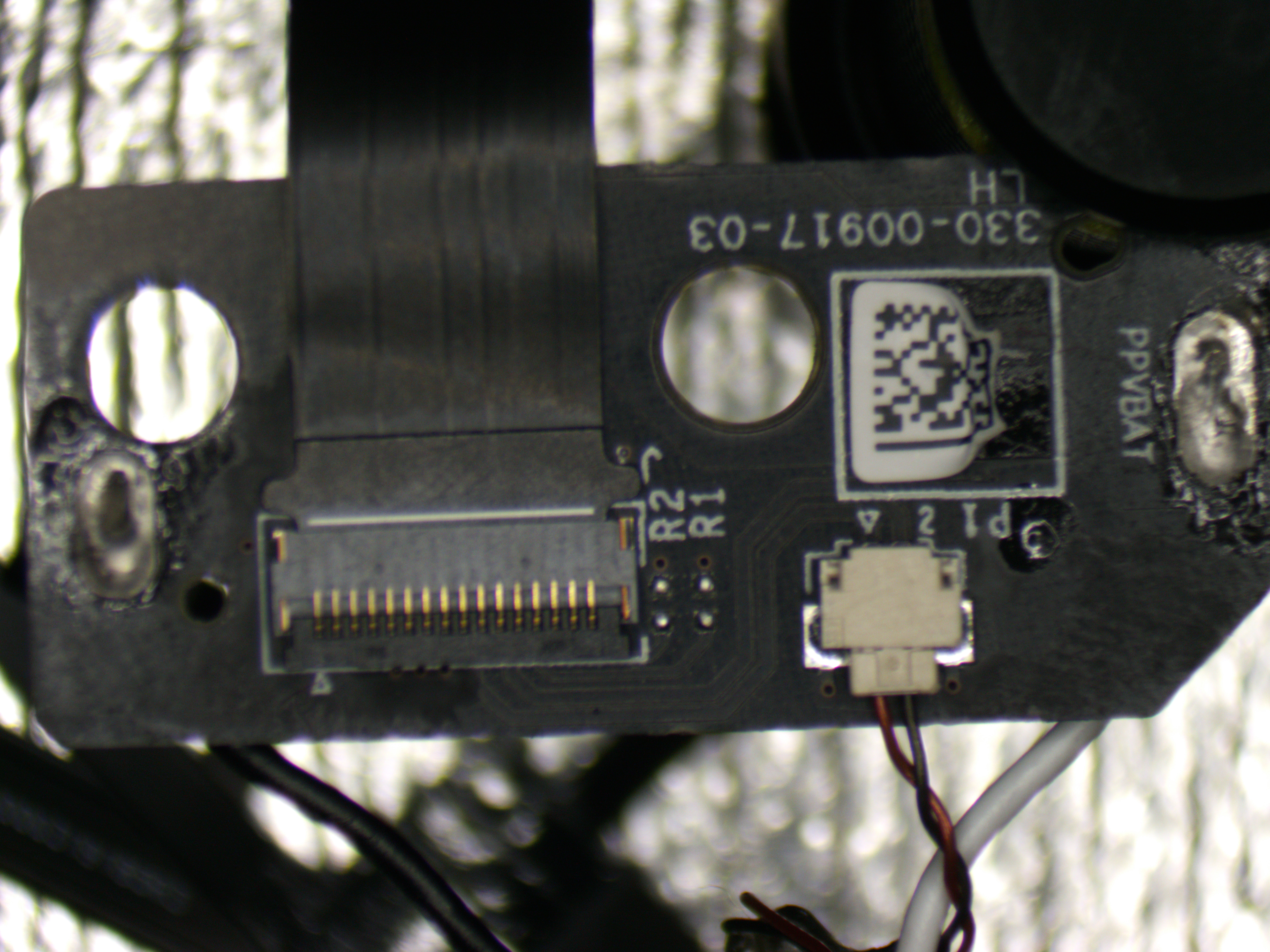
| Name | Pin |
|---|---|
| R2 | SWDCLK |
| R1 | SWDIO |
Mainboard
Bottom side
I pulled out all internal to do a better examination. 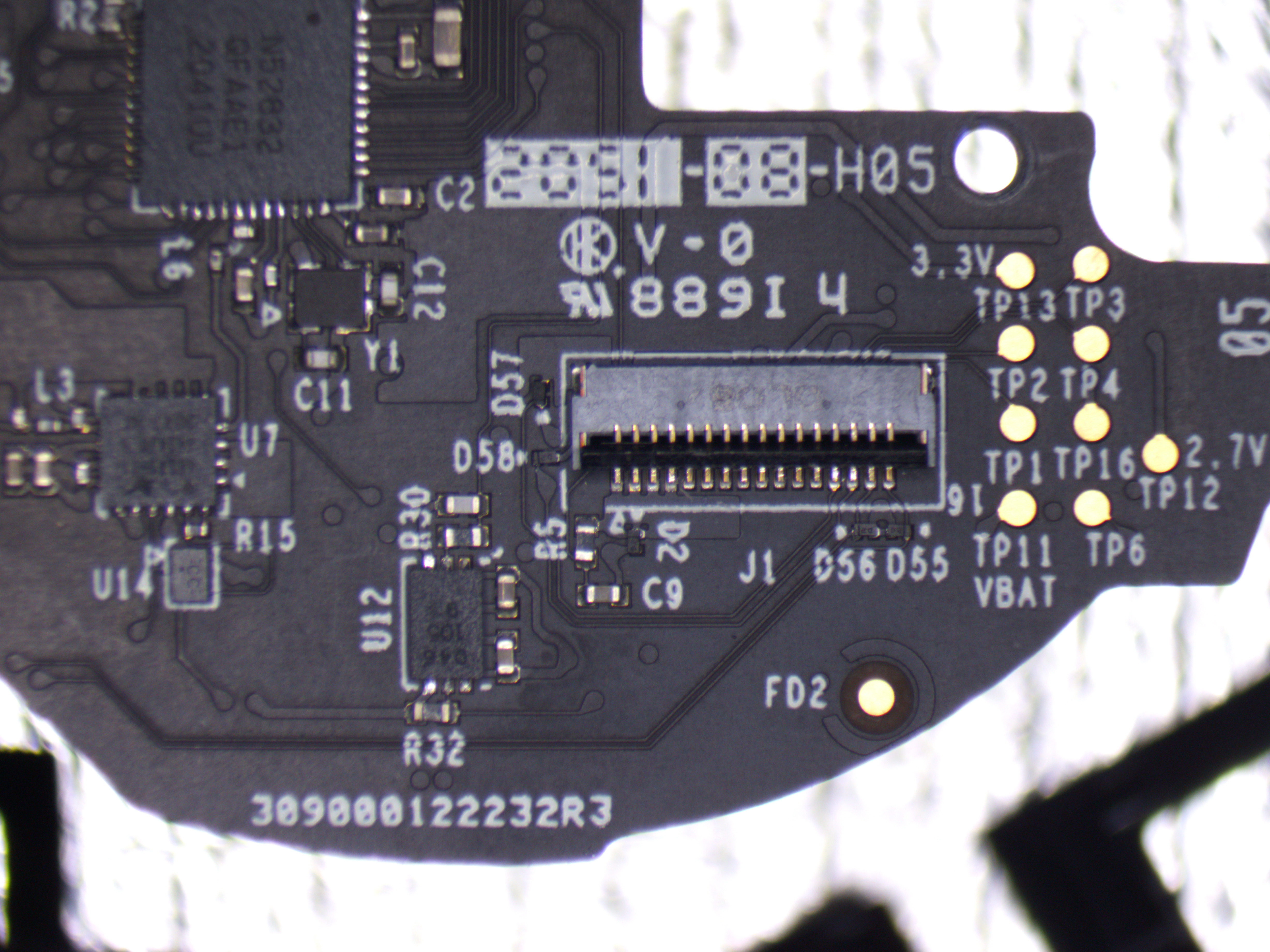
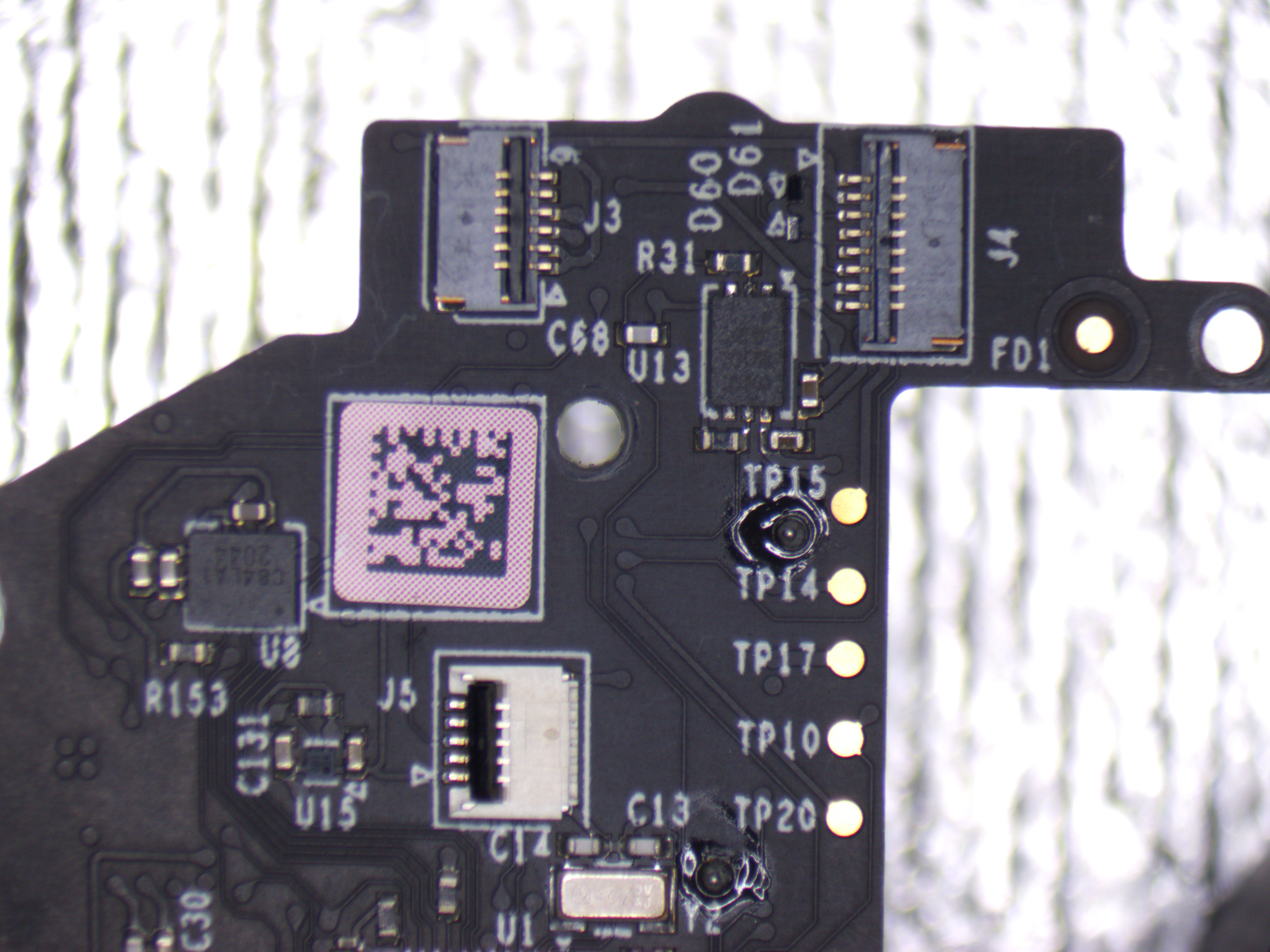
I traced down the TPs:
| Name | Pin |
|---|---|
| TP1 | nrf52 P0.12 - Rx |
| TP2 | nrf52 P0.11 - Tx |
| TP3 | nrf52 SWDIO |
| TP4 | nrf52 SWCLK |
| TP6 | nrf52 P0.04 |
| TP11 | VBAT |
| TP12 | 2.7V |
| TP13 | 3.3V |
| TP16 | GND |
J1 connector is used for connecting the battery pcb.
| Name | Pin |
|---|---|
| TP15 | J4 3rd pin |
| TP14 | ??? |
| TP17 | GND |
| TP10 | nrf52 P0.27 |
| TP20 | J5 1st pin |
J3 and J4 connectors are for LED rings. J5 is for 3D Analog Joystick
J2 is the antenna connector.
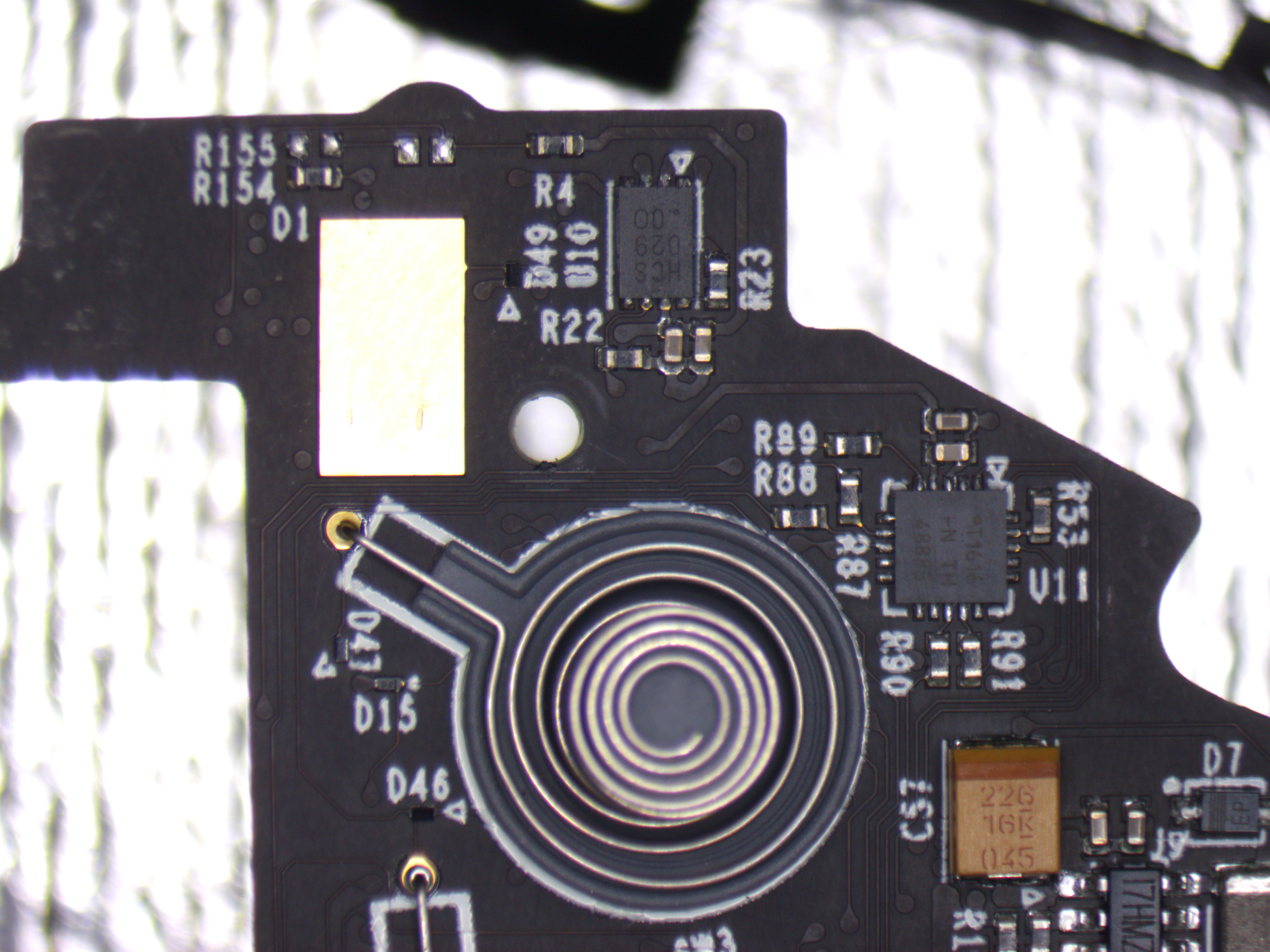
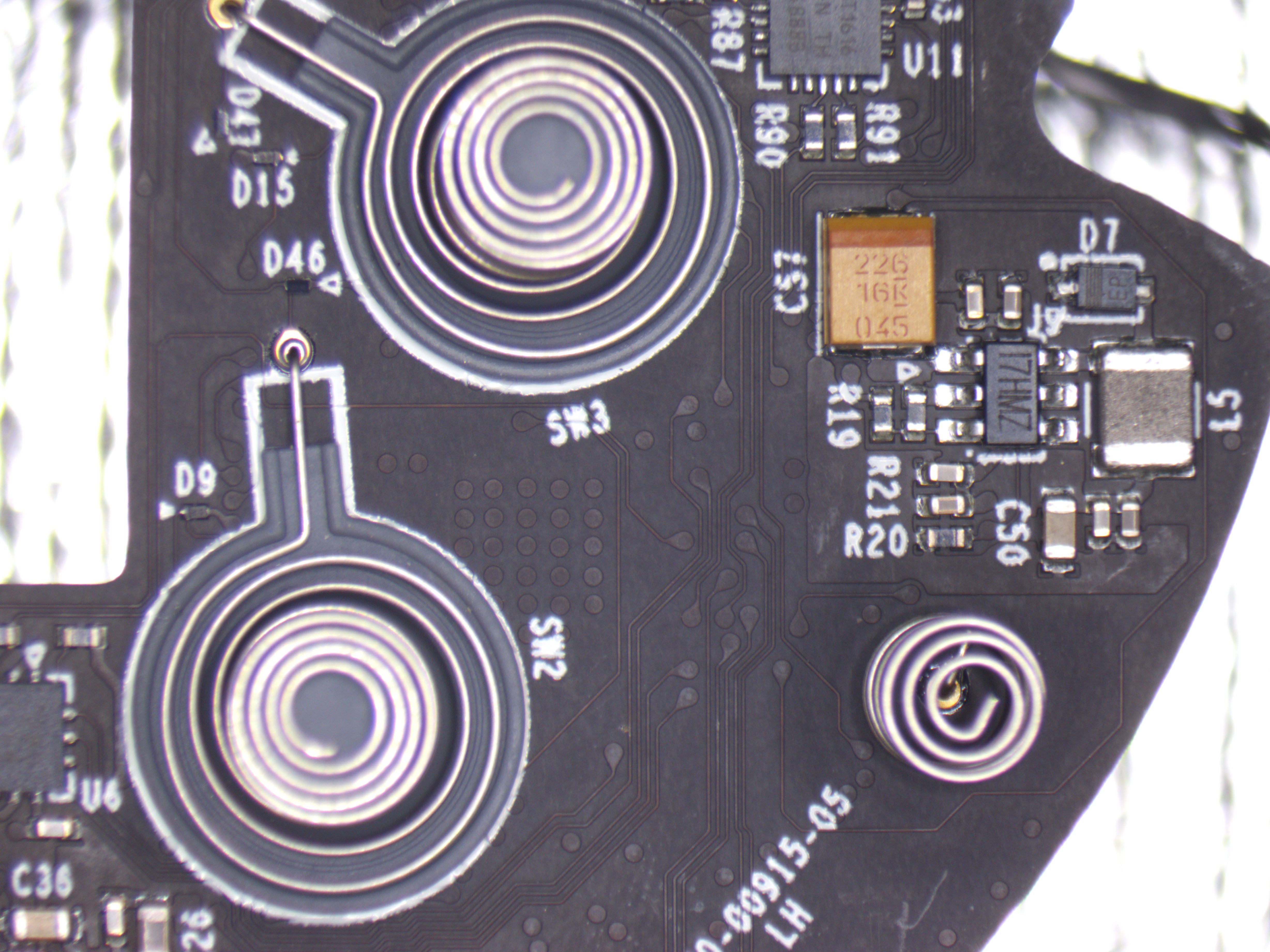
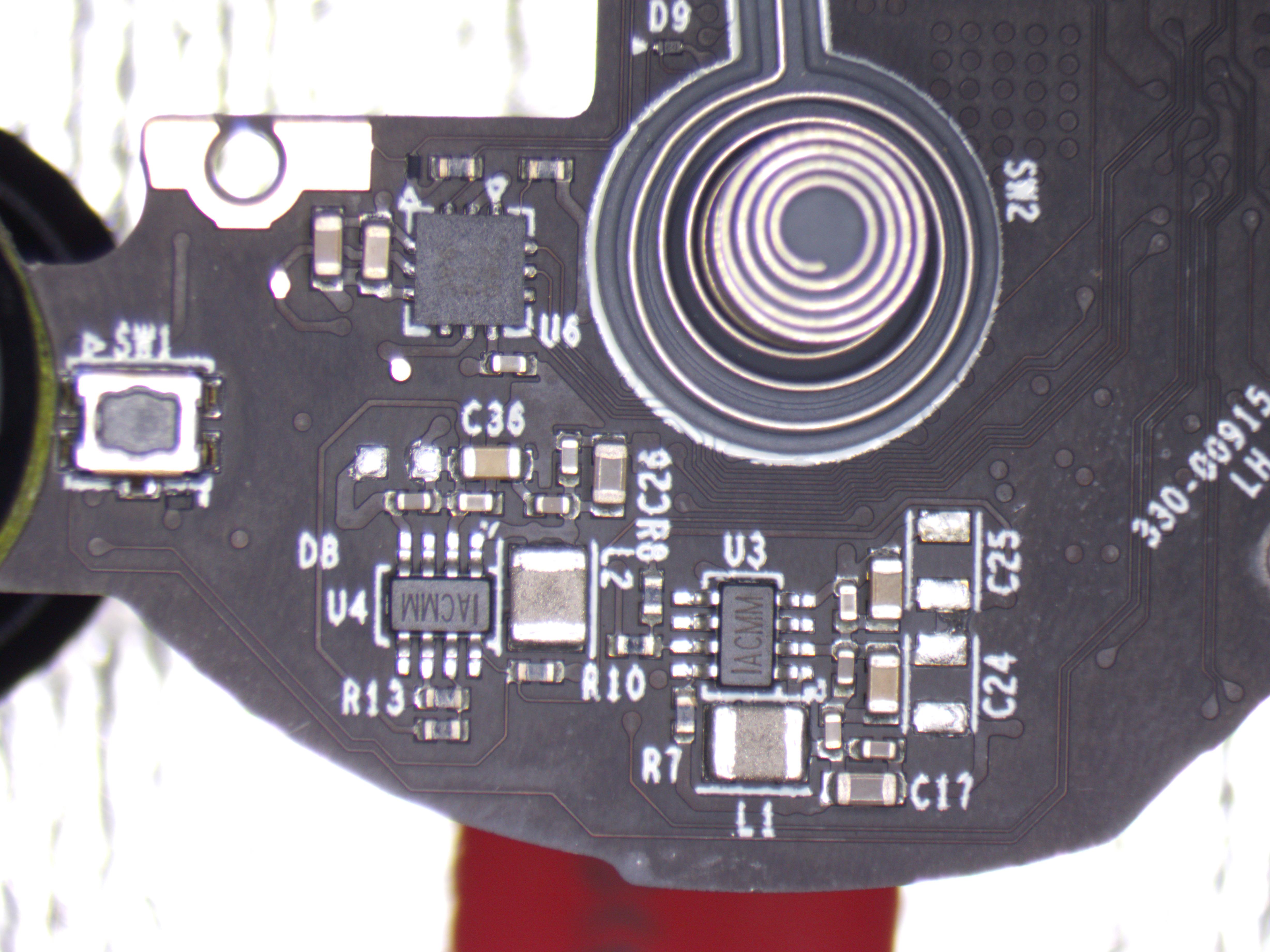
Top side
| Switch Name | Button Name |
|---|---|
| SW3 | Y |
| SW2 | X |
| SW1 | Oculus/Home |
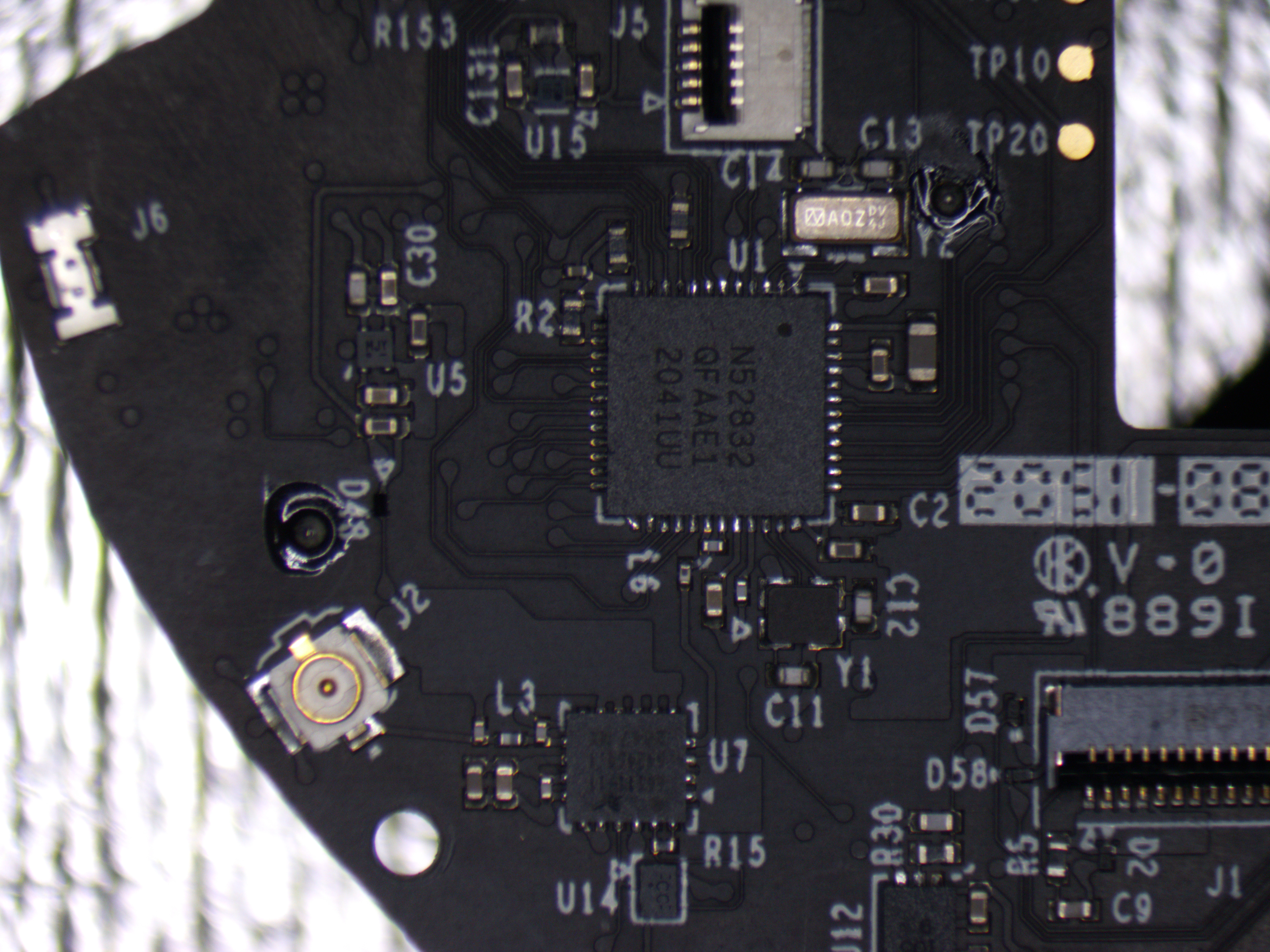
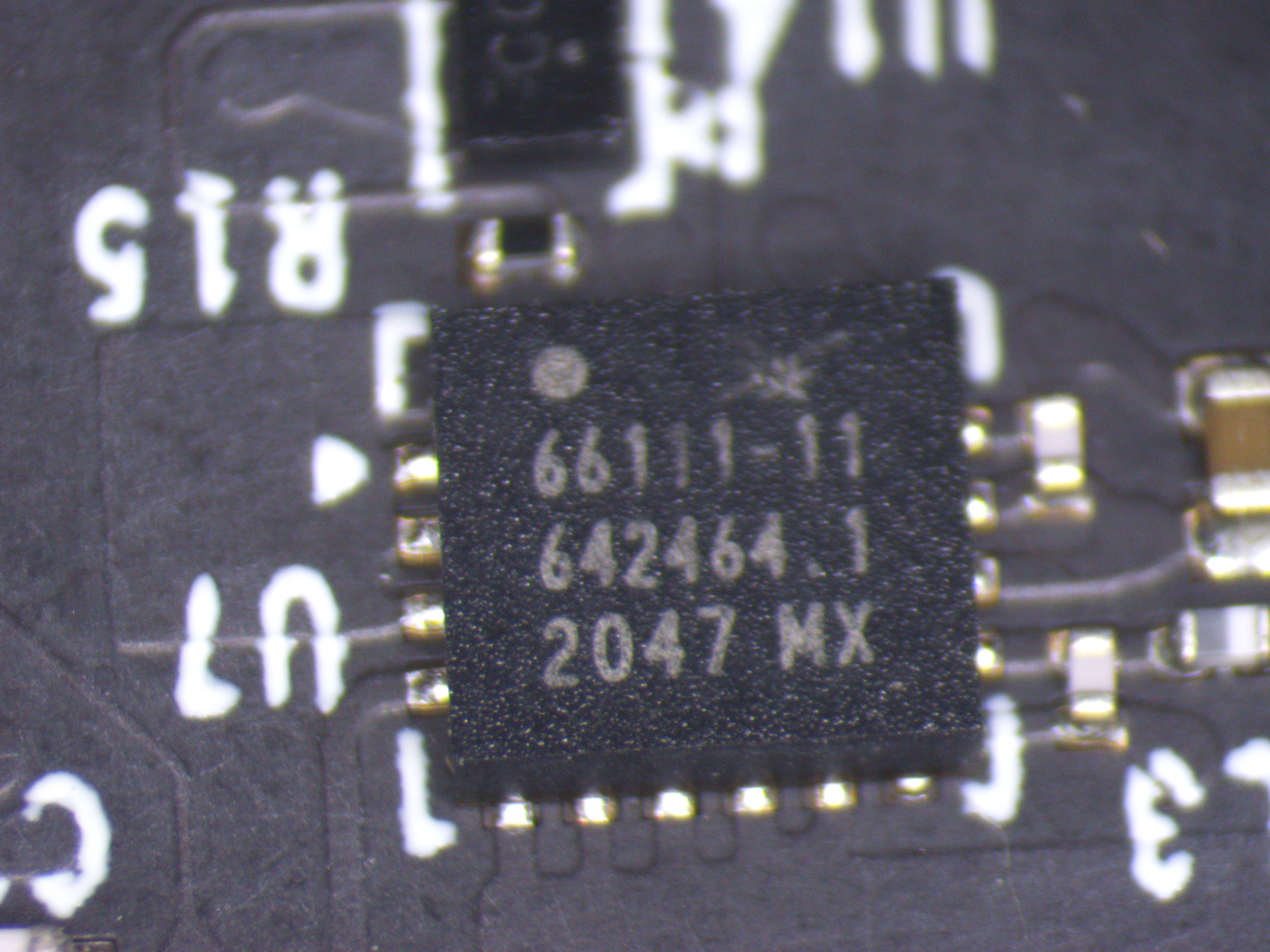
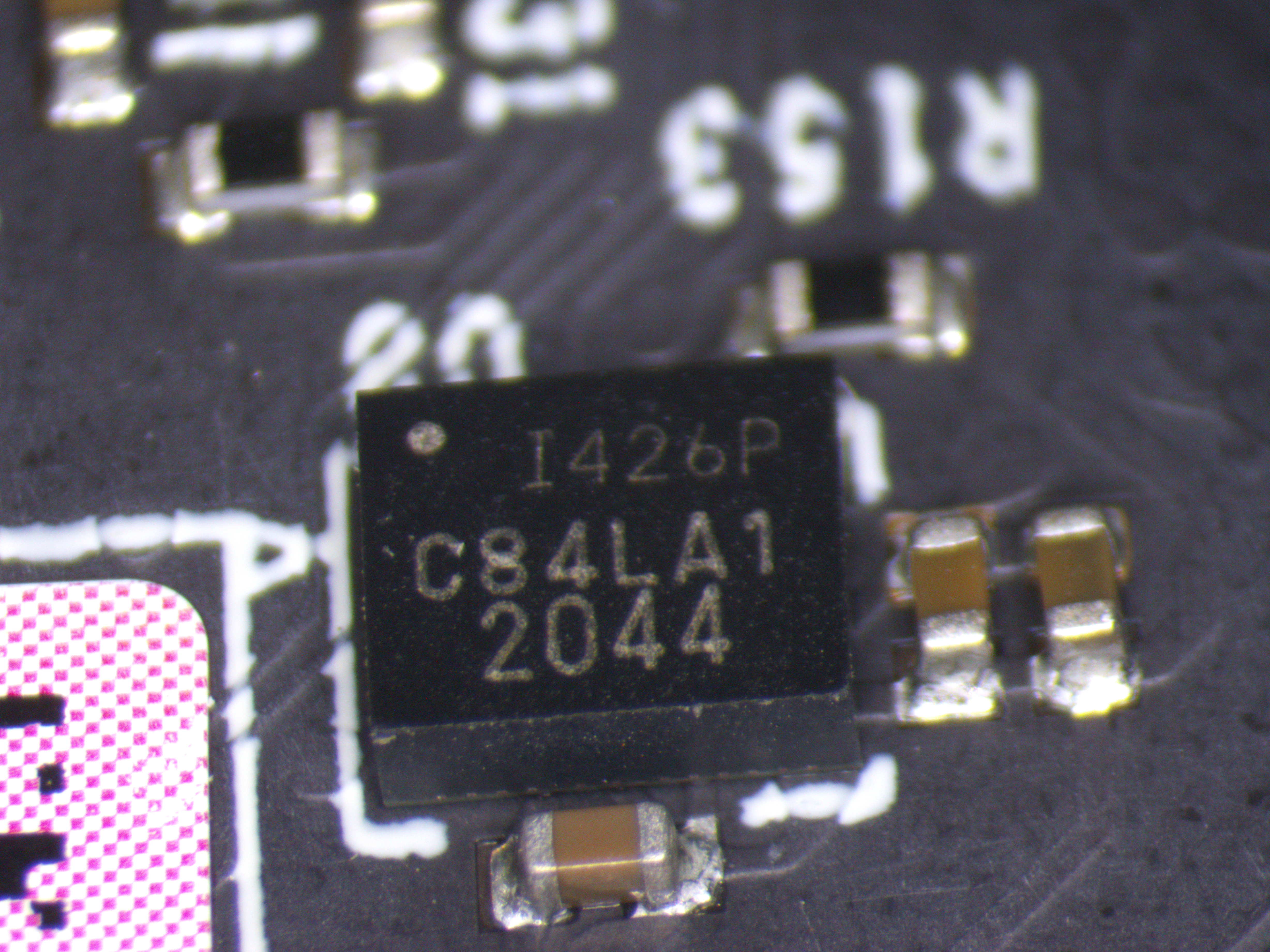
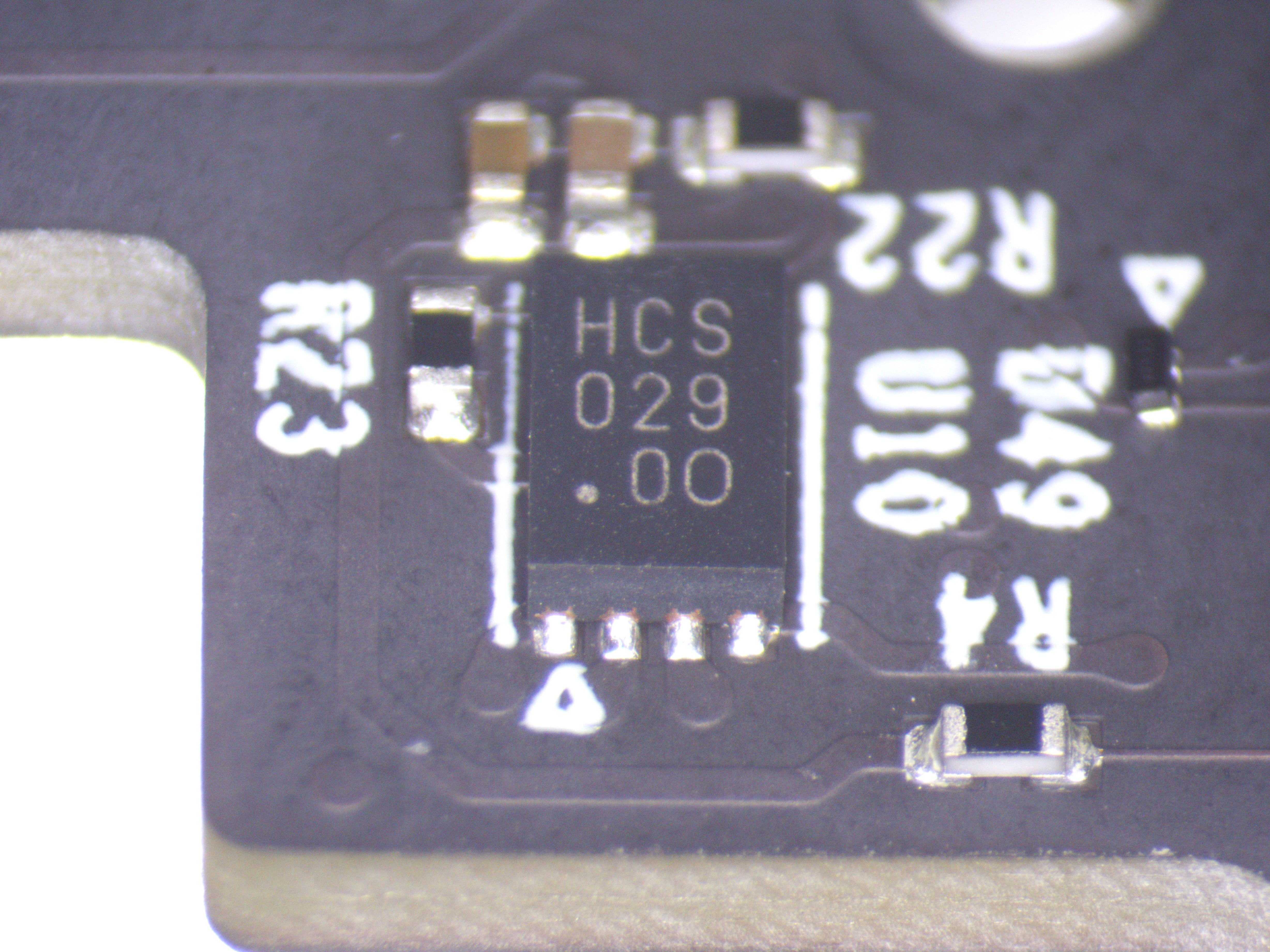
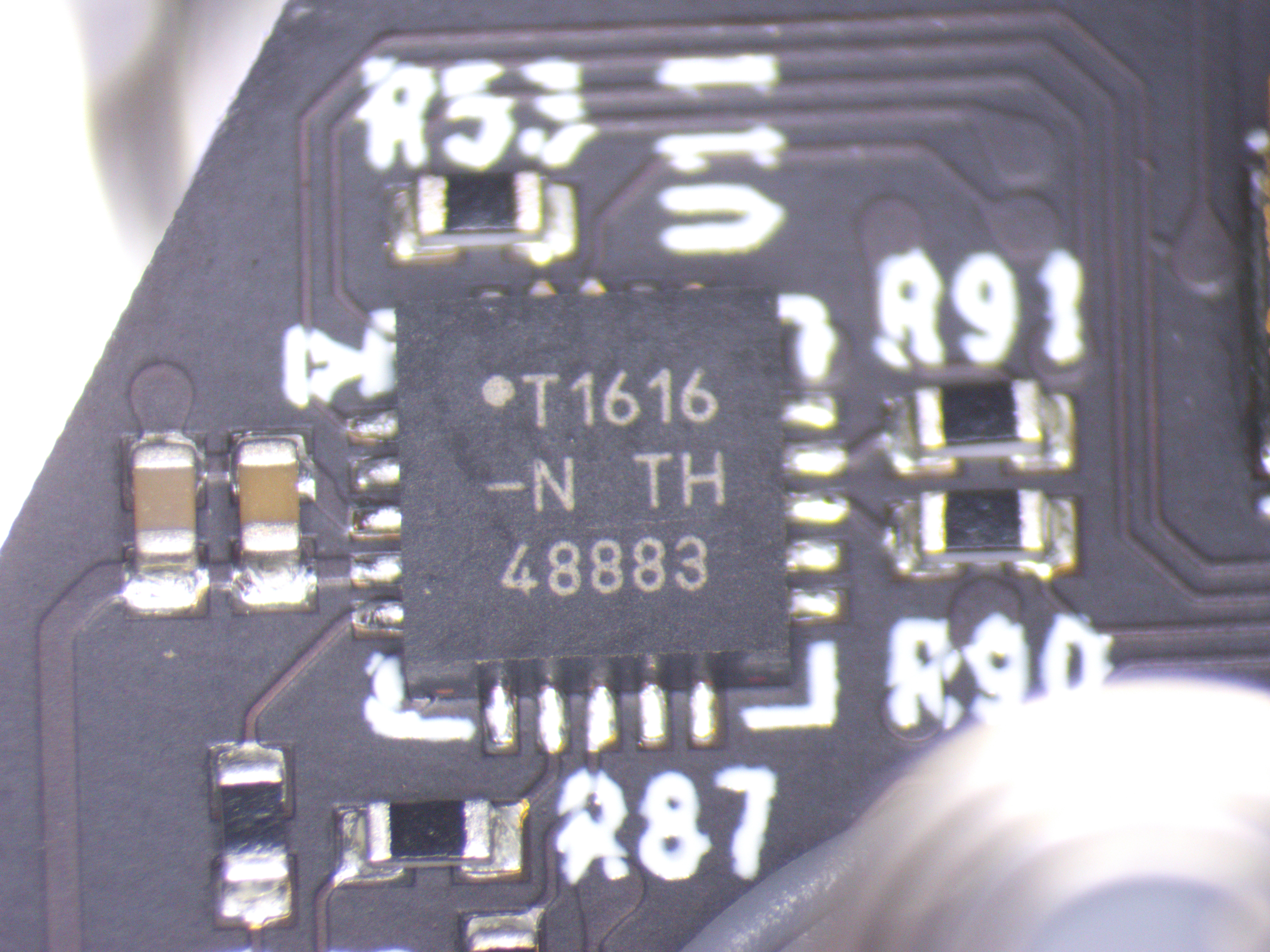
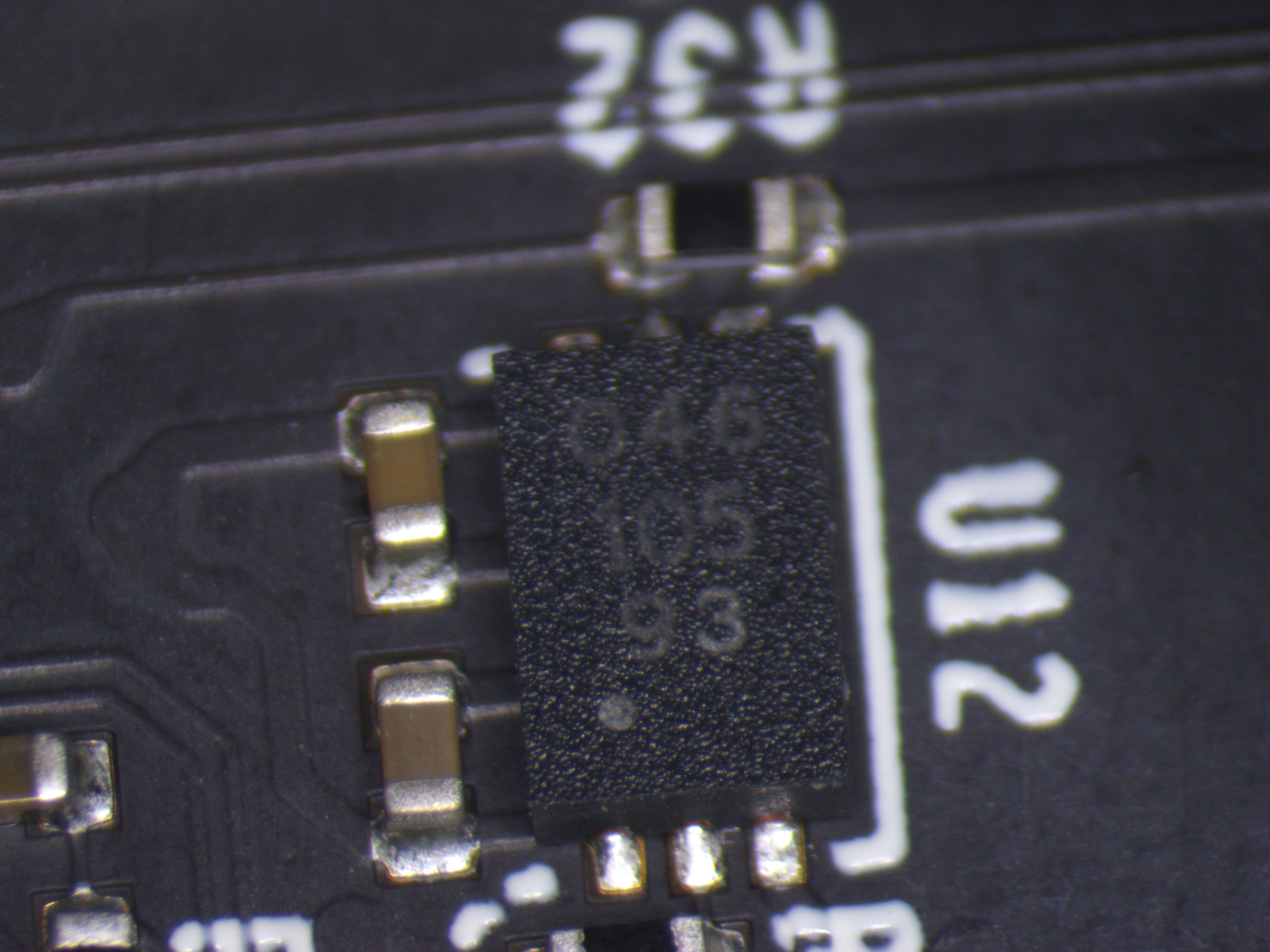
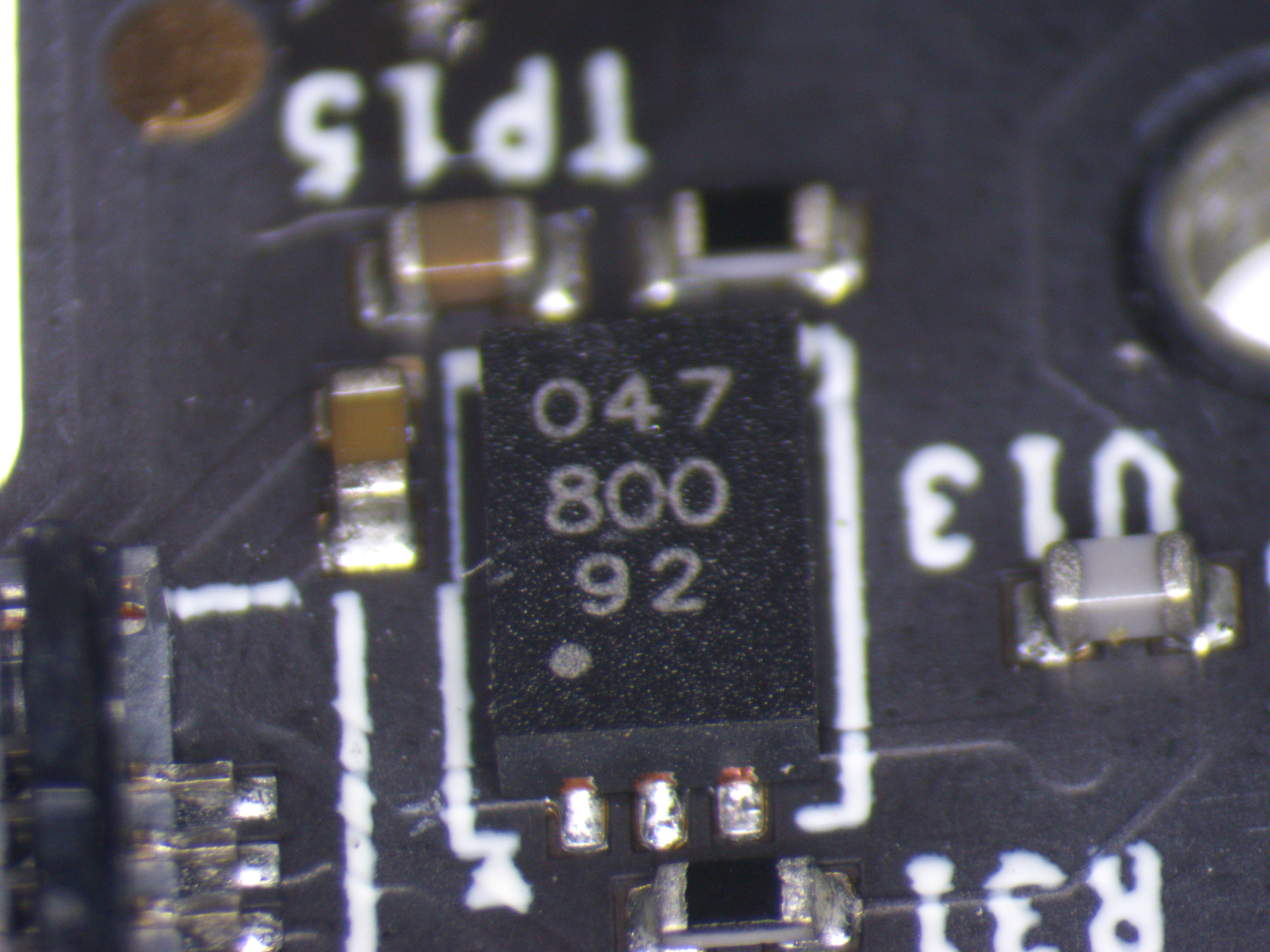
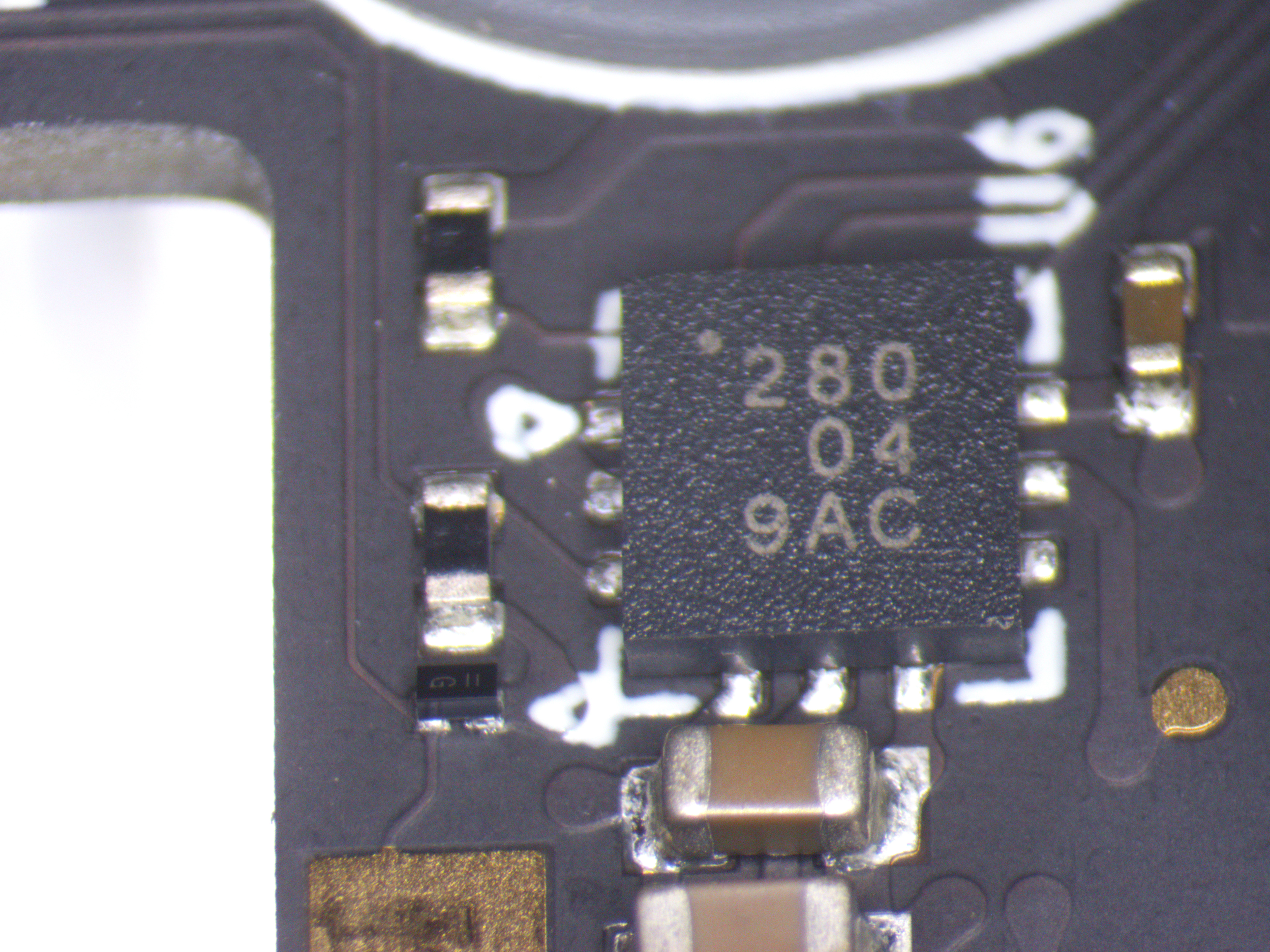
Individual ICs
Summary
The controller is built on the nRF52832 SoC, which, while lacking a verify/secure boot feature, includes read-out protection through the APPROTECT feature. Unfortunately, APPROTECT is activated in the firmware. Fortunately, there’s a known vulnerability that allows for the use of fault injection (voltage glitching) to circumvent the APPROTECT and extract the firmware. Nordic addressed this vulnerability in revision 3 (build code Gx0), but luckily, this controller utilizes an earlier version that still contains the vulnerability.
TODO
Dump the firmware using voltage glitching.